You would be well aware of the necessity for security if you run a business. You also know that compliance with government regulations is critical for your business. In this blog post, we will discuss SOC2 vulnerability management and how it can help your business stay compliant with government regulations. We will also discuss the features of SOC2 compliance and how to implement vulnerability management in your organization. Stay safe and secure – read on!
What Is SOC2 Vulnerability Management?
SOC stands for System and Organization Controls. SOC reports are used by businesses to report on the effectiveness of their internal controls related to security, privacy, and compliance with government regulations.
There are several different types of SOC reports, but in this blog post, we will focus on SOC vulnerability management.
Vulnerability management is the practice of detecting, evaluating, and mitigating security flaws in your computer systems and networks. Businesses must do vulnerability management since it aids them in identifying and repairing security holes before they can be utilized by hackers or other malicious individuals.
Why Is SOC2 Vulnerability Management Important?
There are several reasons why vulnerability management is important for businesses:
– It helps businesses stay compliant with government regulations such as SOX, HIPAA, and PCI DSS.
– It helps businesses protect their systems and data from cyberattacks.
– It helps businesses identify and fix security holes before they can be exploited.
– It helps businesses improve their overall security posture.
Types Of SOC2 Compliance With Explanations
There are three types of SOC2 reports:
– SOC2 for Cybersecurity
– SOC2 for Compliance
– SOC2 for Operational Controls.
SOC for Cybersecurity is the most comprehensive type of SOC report and it covers all aspects of cybersecurity including risk management, security operations, incident response, and data protection. SOC for Compliance is a more limited version of the SOC for Cybersecurity report and it focuses on compliance with government regulations such as SOX, HIPAA, and PCI DSS. SOC for Operational Controls is the least comprehensive type of SOC report and it focuses on the operational controls used by businesses to protect their systems and data.
SOC Compliance- Which Type To Choose?
This is a concern that must be addressed based on your company’s needs. If you are a business that is required to comply with government regulations such as SOX, HIPAA, and PCI DSS, then you will need to have a SOC for a compliance report. If you are a business that is not required to comply with government regulations but wants to improve its overall security posture, then you will need to have a SOC for Cybersecurity report.
How Can Vulnerability Management Help with SOC2 Compliance?
Vulnerability management can help businesses stay compliant with SOC2 by identifying and fixing vulnerabilities in their systems. Businesses can reduce the risk of a data breach or other security incident that might result in regulatory compliance infractions by addressing these flaws. What are the features of SOC compliance? Let’s take a look!
Features of SOC2 Compliance
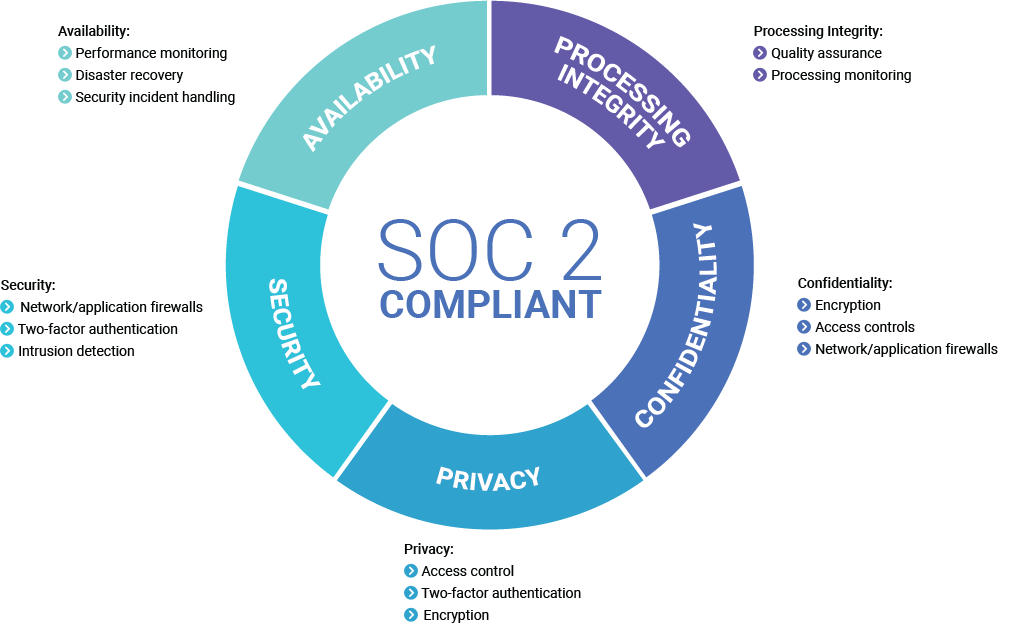
There are several features of SOC2 compliance that business owners should be aware of:
– The SOC framework is based on the ISO/IEC 27002 standard.
– SOC compliance is based on a risk-based approach.
– The Security, Privacy, Availability, Processing Integrity, and Confidentiality domains make up the SOC framework.
– The SOC framework is flexible and can be tailored to meet the specific needs of your organization.
Tips for Managing Vulnerabilities in Your Organization
Here are some tips for managing vulnerabilities in your organization:
- Use a vulnerability management solution to identify and fix vulnerabilities in your systems.
- Train your employees on how to spot and report security flaws.
- Patch your systems and applications regularly.
- Ensure that your antivirus software is up-to-date.
- Strong passwords and two-factor authentication are recommended.
- To safeguard your systems, install firewalls and other security measures.
- Establish policies and procedures for vulnerability management.
- Regularly test your security controls to ensure that they are effective.
Tools for Managing Vulnerabilities in Your Organization
Here are some tools for managing vulnerabilities in your organization:
– A vulnerability management solution, such as QualysGuard, can help you identify and fix vulnerabilities in your systems.
– Employee training can help you teach employees how to identify and report vulnerabilities.
– Policies and procedures for vulnerability management can help you establish a process for managing vulnerabilities in your organization.
– Regular testing of your security controls can help you ensure that they are effective.
Conclusion
In this blog post, we looked at the features of SOC2 compliance and how vulnerability management can help businesses stay compliant. We also looked at some tips for managing vulnerabilities in your organization and some tools for helping you do so. Stay safe!
Read more: 5 Benefits Of Using A VPN





